
V Laboratoři vestavné bezpečnosti se zabýváme všemi aspekty bezpečnosti vestavných zařízení. Dnes počítačové systémy řídí nejen automobily, vlaky, ale také chytré domácnosti nebo celá města. Pro zajištění bezpečnosti těchto často autonomních systémů, v IoT prostředí navíc omezených požadavky na malou velikost i spotřebu, je korektní implementace kryptografických algoritmů kritickou záležitostí.

Čemu se laboratoř věnuje?
Věnujeme se bezpečnosti Internetu věcí, kyber-fyzikálních systémů a vestavných systémů. Mezi naše výzkumná témata mj. patří:
- Návrh kryptografického hardwaru, hlavně v programovatelných hradlových polích (FPGA).
- Kryptoanalýza, tedy útoky,
- ať už s využitím programovatelného hardware (FPGA) nebo
- prostřednictvím postranních kanálů, a
- účinná ochrana proti takovým útokům.
- Ochrana vestavných systémů s mikroprocesory (Internet věcí, čipové karty, …).
- Spolehlivost kryptografických systémů.
Činnost laboratoře se dotýká těchto témat
Co máme za sebou?
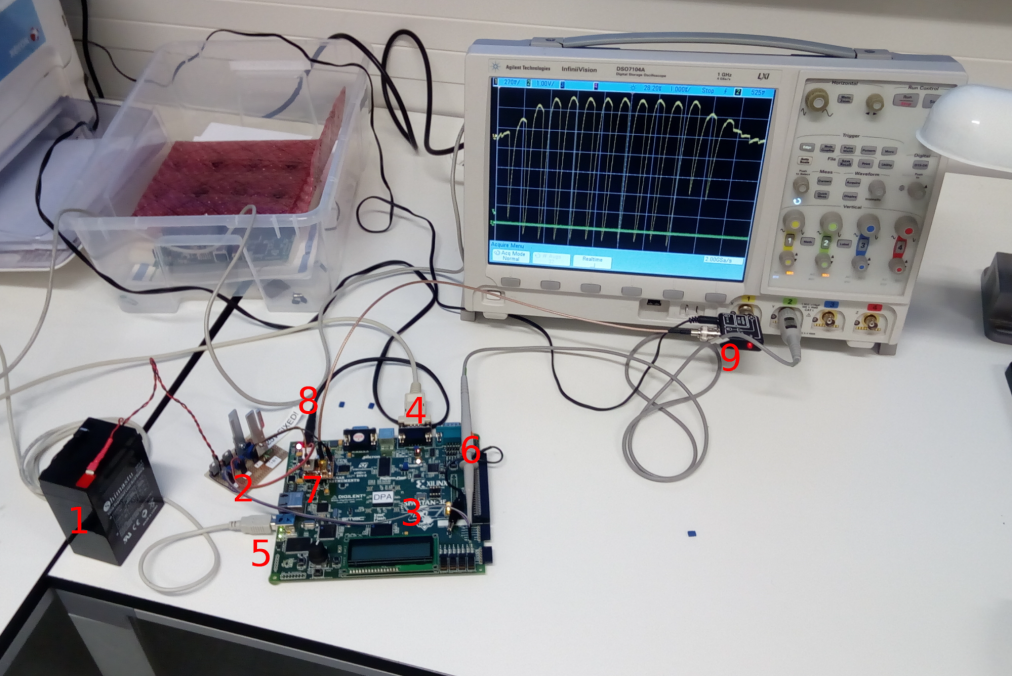
Jak to u nás vypadá
Kontaktní osoba

- +420224358715
- novotnym@fit.cvut.cz
- TH:A-1033
Kde nás najdete?
Laboratoř vestavné bezpečnosti
Katedra číslicového návrhu
Fakulta informačních technologií
České vysoké učení technické v Praze
Místnost TH:A-1058 (Budova A, 10. patro)
Thákurova 7
Praha 6 – Dejvice
160 00

